October 24, 2023
Castelldefels, Barcelona 16-17 October 2023: The third ETSI TeraFlowSDN (TFS) Hackfest was held in Castelldefels, Barcelona, Spain. We had two days of hands-on experience with the TFS controller and specific focus in P4. During the first day, a walkthrough of the installation procedure of TFS was presented followed by a small demo utilizing the main abstractions of the Controller (device, service, and policy layer) that showcased some of the functionalities that TFS provides. In the second day, participants delved deeper into both TFS and P4, by trying to build various programs that calculate the latency of a service and report it to the Monitoring component of TFS. All in all, the whole experience was really interesting with a lot of involvement from the community and participants.
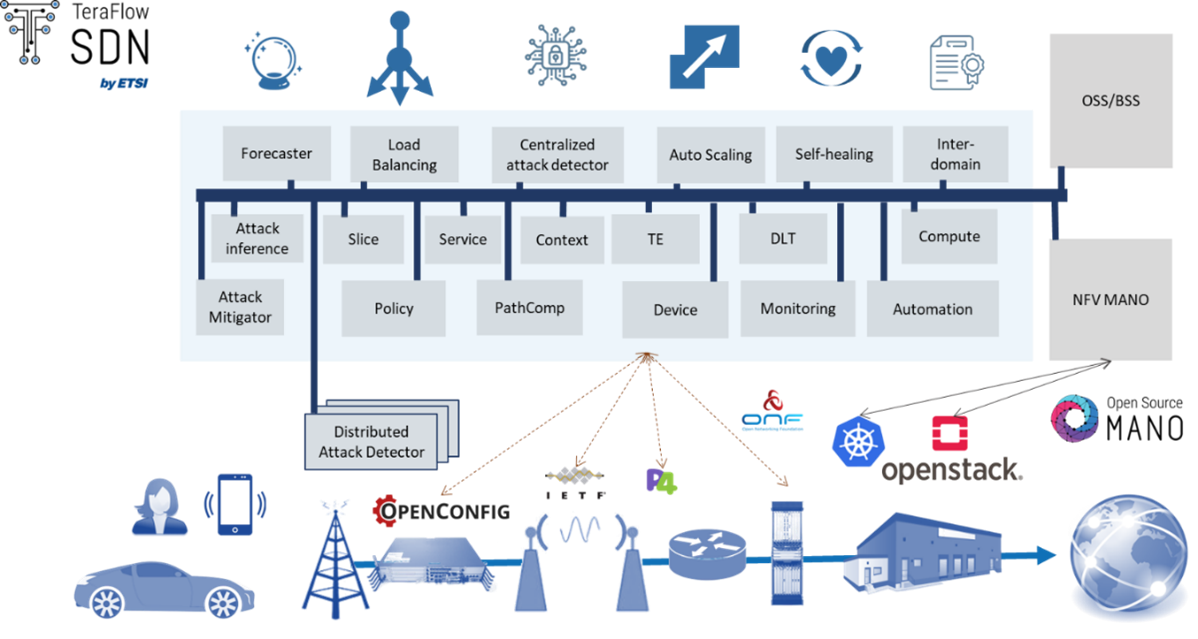
ETSI TFS#3 Hackfest - Day 1 The first day began with two presentations about the internals of the TeraFlowSDN controller. Georgios P. Katsikas, went into detail through the architecture of TeraFlowSDN, the various components and how they work together. Additionally, he described the main layers and their abstractions that are used by TFS to make the management of a network easier: Device, Service and Policy layers. The Device layer forms the basic interface between the controller and the managed devices. The SBI component, which is at the heart of the Device layer, exposes a common API for all the different classes of network devices. This API is implemented by different device drivers, each tailor-made to allow TFS to control a specific class of devices, such as P4 whiteboxes, openconfig routers, etc.
Higher in the TFS architecture, there is a Service layer, which establishes (end-to-end) connectivity services across a large number of devices. The basic assumption is that every service is a connection between two endpoints in the network. Services can be tied to specific values or conditions that need to be satisfied, like SLAs or QoS. These constraints are first passed through the Path Computation component, which finds an appropriate path. Then this path is passed to the Service component which translates the service intent to specific rules that should be installed to the underlying devices. Finally, the Policy layer utilizes the Monitoring component’s alarm mechanisms to make sure that specific KPIs are within thresholds. In case of an alarm, indicating an abnormal KPI value, the Policy component is triggered to instruct the Service component for any changes that need to happen to ensure SLA compliance.
In the second presentation, Panagiotis Famelis showcased all of the above abstractions in a complete P4-based demo. This work was demonstrated at the IEEE HPSR 2023 conference where the authors appeared with a demo paper, poster, and video. The demo first began with an explanation of the steps to install the TeraFlowSDN controller and of the various parameters that can be configured. Mininet was used to simulate a small network with a ring topology of P4 switches and establish a service between two endpoints in it. On top of that a monitoring mechanism was established, which calculated the latency of the selected service path, using a simple ping mechanism and relayed that information to the Monitoring component. Finally, a policy was set, to trigger a path recalculation in case a certain latency threshold is exceeded, and was tested using unix traffic control to insert latency to the original service path. That demo wrapped up the first day of the Hackfest which was more focused on tutorials.
ETSI TFS#3 Hackfest - Day 2 The second day of the Hackfest focused on hands-on activities. Panagiotis began by explaining the internals of the monitoring mechanisms and guided participants to write their own similar programs. The various protobuf files, which define the gRPC APIs of the TFS components, were described and analyzed. While the focus was on Monitoring and Context protobufs, participants were able to understand their significance as a guide when developing scripts that communicate directly with TFS components. Based on that knowledge, participants were able to replicate the original monitor mechanisms and extend it so that it can measure and register a new KPI (i.e., packet loss).
Up this point, P4 was mainly used as an underlay, but in the last session, the focus was on P4 itself. The instructors went over the basic idea of a P4 program and guided participants into understanding the program that had been used until then. Then we took it one step further. A new program, with missing parts, was given to participants with some primitive in-band telemetry (INT) mechanisms, which recorded the path a packet took in the network. Instructions on how to build the source code and set the new configuration to the switches were given and participants were able to try their intuition on how to fill in the missing parts. With a working source code, the focus now was on how to make this new program work with the TFS Service component. The internal mechanisms of the P4 service handler were discussed and as a final step participants managed to change the existing service handler in order to accommodate the new P4 program they had built. The 3rd Hackfest closed with a presentation about P4 in-band telemetry (INT), its various modes and its uses, together with a roadmap on how TeraFlowSDN plans to support it in the forthcoming releases.
ETSI TFS#3 Ecosystem Day The TFS#3 Hackfest was followed by the TFS#3 Ecosystem Day on Wednesday 18 October, where representatives from SNS Research projects and ETSI Software Development Groups exchanged on their plans for using and contributing to TeraFlowSDN.
Summary In summary, the Hackfest was very interesting and fun! The organization of the event by ETSI was great, our hosts at CTTC did an awesome job at accommodating the various needs for the different events and the instructors from UBITECH, shared their expertise on a wide range of topics ranging from TeraFlowSDN-specific mechanisms to P4-related features: big thanks to all for that!
All the hackfest material is available in the wiki.